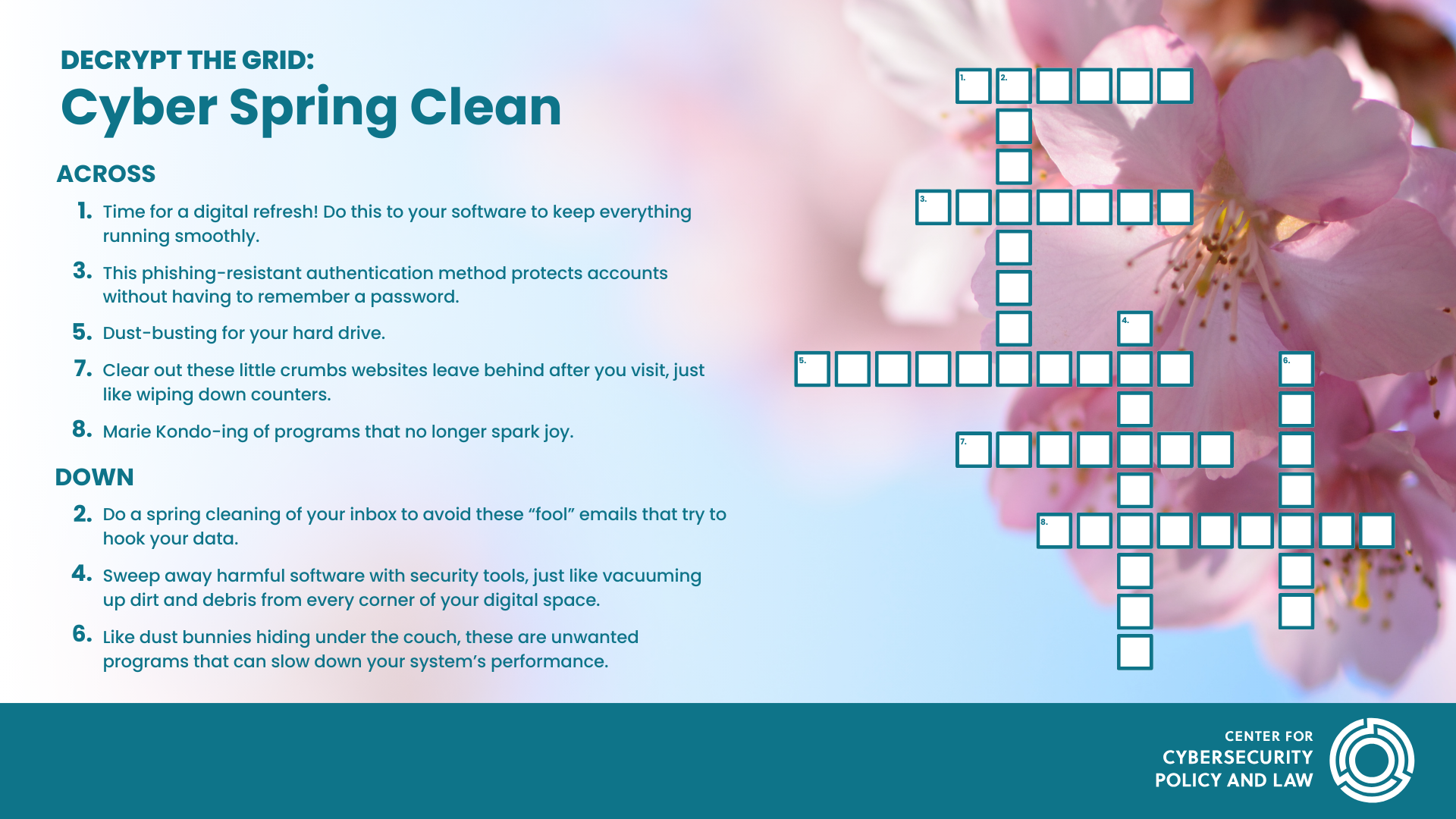
Across:
1. Time for a digital refresh! Do this to your software to keep everything running smoothly.
3. This phishing-resistant authentication method protects accounts without having to remember a password.
5. Dust-busting for your hard drive.
7. Clear out these little crumbs websites leave behind after you visit, just like wiping down counters.
8. Marie Kondo-ing of programs that no longer spark joy.
Down:
2. Do a spring cleaning of your inbox to avoid these “fool” emails that try to hook your data.
4. Sweep away harmful software with security tools, just like vacuuming up dirt and debris from every corner of your digital space.
6. Like dust bunnies hiding under the couch, these are unwanted programs that can slow down your system’s performance.
Read Next
Cybersecurity Coalition, Hacking Policy Council Comment on NIST Cyber AI Profile
The Cybersecurity Coalition and the Hacking Policy Council submitted comments to NIST in response to the initial public draft of the Cybersecurity Artificial Intelligence Community Profile.
Special Episode: A Look at Cyber Policy in 2026 (DCP S2 E12)
For our second special episode of the Distilling Cyber Policy podcast, Alex and Jen from the Center are joined by experts to try and predict the future of cyber policy in the coming year, while reflecting on some of their previous prediction.
Offensive Cyber Operations with Stacy O’Mara and Leonard Bailey (DCP S2 11)
Offensive cyber activity has become a central policy conversation as governments worldwide rethink what tools are necessary to counter increasingly sophisticated threats.

