“In times of great uncertainty, people don’t need more data. They need more clarity.” – Scott Cook (Intuit co-founder)
Having worked in federal cyber policy circles for the last two decades, I’ve observed a recurrent trend. A large-scale cyber intrusion or attack dominates headlines. Experts lament the nation’s inability to prevent such incidents. Some voices call — often with more rhetoric than detail — for the private sector to be unleashed against U.S. adversaries. Debate follows. And then … nothing changes. The cycle repeats.
We’re once again in the midst of this familiar cycle, prompted by headline-stealing cyber incidents like Volt and Salt Typhoon. But this time may be different. Prior administrations, Democratic and Republican, have batted away proposals to authorize the private sector to mount sanctioned cyber attacks against the country’s adversaries. The Trump Administration has not formally endorsed such measures, but officials have signaled support, and a bill introduced this year would allow the government to authorize private cyber operations through the issuance of constitutionally recognized Letters of Marque.
If these proposals are to be seriously considered, policymakers will need to confront a host of unresolved issues. The nuts and bolts of these proposals remain vague, leaving fundamental questions unanswered:
- What legal protections would private actors receive?
- What safeguards would be required to prevent operations from causing unintended harm that undermines U.S. cybersecurity or national interests?
- Which agency or authority would be responsible for reviewing and approving operations?
- What assurances, if any, could the U.S. government provide against prosecution by foreign authorities when actions target servers abroad?
And these represent only a subset of the most pressing questions.
All of this underscores the need to interrogate these proposals with greater rigor and to distinguish between workable options and those that are more aspirational than practical. This is the first in a series of posts that will attempt to do just that, examining the terminology, purposes, operational frameworks, historical antecedents, and potential liability protections relevant to public-private cyber operations. But before diving in, let’s start with a few preliminary observations.
Who Wants This?
These proposals often appear to enjoy more support than they command. Historically, factions of Congress dissatisfied with the status quo have pushed for empowering the private sector to adopt a more offensive cybersecurity posture. The Active Cyber Defense Certainty Act, first introduced in 2017 and reintroduced in 2019, represented the first legislative attempt to explicitly authorize private-sector cyber operations. The bill never advanced to a floor vote and has not been reintroduced since. (A detailed analysis of this bill will follow in a later post.)
More recently, Congress considered a bill that would authorize the issuance of constitutionally prescribed Letters of Marque — the first time so-called “cyber Letters of Marque” have been formally raised for legislative consideration. Like its predecessor, the proposal attracted some bipartisan interest. Whether it will gain traction in Congress, particularly with support from the Trump Administration, remains to be seen.
Assessing private-sector appetite for offensive cyber operations is even more challenging. Historically, support has been muted. Today, some well-established and emerging cybersecurity firms — particularly those whose business models and service offerings align with offensive capabilities — are among the most vocal advocates for expanding private-sector involvement.
Industry-at-large, on the other hand, seems less enthusiastic. While the idea of a more aggressive posture to defend U.S. assets has popular appeal, there is little consensus within the private sector about its proper role in such efforts. Most CEOs and boards do not view battling adversaries, such as Iran’s Islamic Revolutionary Guard Corps or Russia’s Federal Security Service, to be in their corporate charter. And they are generally unprepared — and unwilling — to assume the risks that such operations would entail.
So, Does the Premise Make Sense?
Regardless of whether broad industry consensus exists, there is clear value in improving the operational integration of willing private-sector partners with government cyber efforts. This is not a new idea. In fact, it dates back nearly 15 years to the government’s disruption of the Coreflood botnet with industry assistance, and it continues today through routine collaborations on takedowns and disruption campaigns — more than 30 such operations since 2020 alone. Yet despite these successes, these efforts have largely remained ad hoc rather than evolving into a more structured model of operational cooperation.
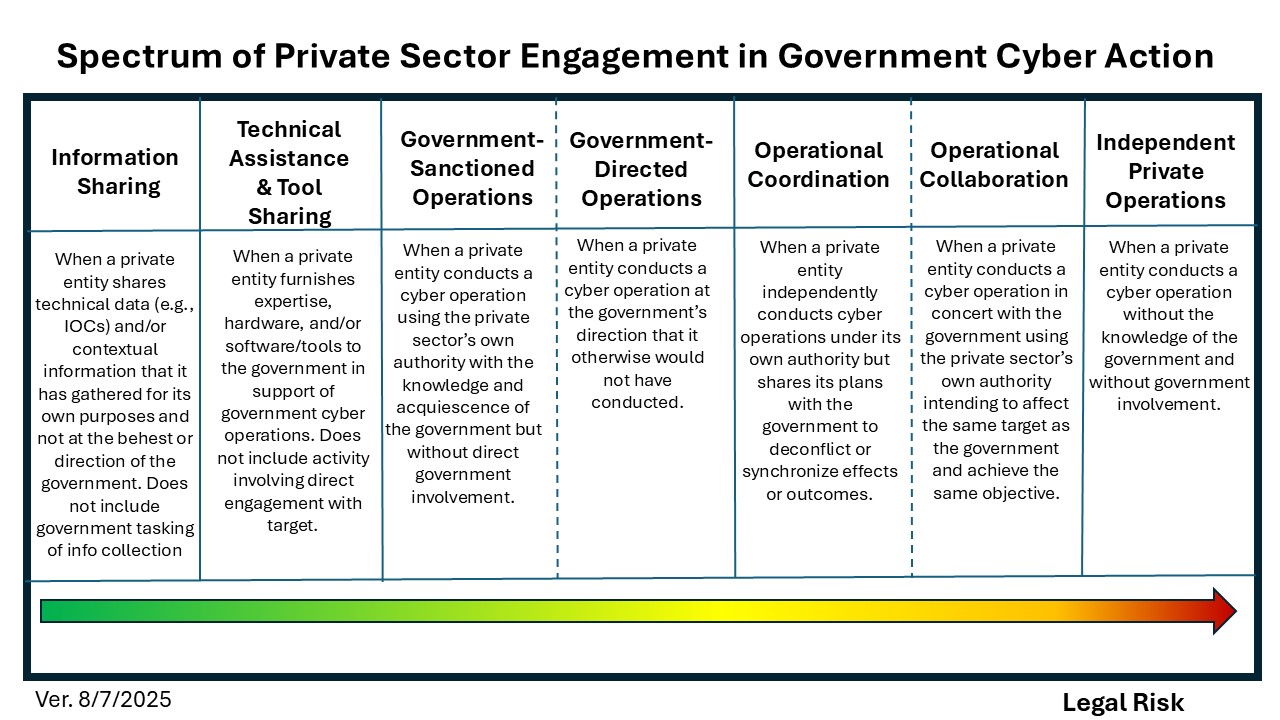
My experience working both inside government and alongside the private sector reinforces a simple truth: impactful cybersecurity is a team effort. Many of the most successful initiatives in U.S. cyber defense — such as improved threat information sharing, refined approaches to risk management, informed standards-setting processes, and advances in protecting critical infrastructure — are the direct result of sustained public-private collaboration.
Still, while these partnerships have proven their value in many areas, the leap to formalized cooperation in actual cyber operations has remained elusive. And the reasons for that hesitation are not only understandable — they are well-founded. Why?
What’s Holding Them Back?
The principal factors dampening private sector enthusiasm for cyber operations are risk and uncertainty. Anyone who has professionally planned or assessed government cyber operations knows that even the simplest ones can raise thorny, unresolved legal and policy questions. And when you add the private sector involvement into the mix, things get even messier. Some of the big unresolved questions look like this:
- Does the government create a loophole that circumvents legal restrictions by acting through a private company?
- At what point does collaboration turn into “state action” that triggers constitutional protections and prohibitions?
- Does collaboration with the government trigger legal protections and, if so, to what degree?
- What sort of protection from international laws will a company working in concert with or at the direction of the government receive?
The lack of clear answers has dogged efforts to institutionalize joint cyber operations for years. And here’s the blunt truth: CEOs, C-Suites, and General Counsels will not assume ill-defined risk.
But legal uncertainty isn’t the only issue. Proponents of joint cyber operations often argue that sidelining private companies is like “fighting with one hand tied behind our back” and wasting the opportunity to thwart our adversaries. It sounds great as a rallying cry—but it’s more slogan than settled fact. The real question is whether unleashing private sector operators actually improves national cybersecurity or just creates new problems. To figure that out, we need more analysis on questions like:
- When is investing in enabling private sector ops more effective than just hardening defenses?
- If companies are empowered to act, does that increase the number of operations, even though many cyber operations are opportunistic rather than engineered?
- Given that adversaries often use disposable infrastructure, how much impact would private ops really have?
- Would encouraging U.S. companies to hack foreign systems establish international norms that backfire — especially since the U.S. has the largest cyber-attack surface on the planet?
There would be more enthusiasm, and less debate, if we had answers to these types of questions.
What’s to Come
This post kicks off a series that will unpack these questions and explore practical approaches for public-private collaboration in cyber operations. We’ll shine light on the gray areas, sort through the questions systematically, and try to build a more solid foundation for the debate. Next up: a dive into the terminology and lexicon that shape how we talk about “cyber operations.”
Leonard Bailey is a fellow for the Center for Cybersecurity Policy & Law and served as a federal prosecutor at the U.S. Department of Justice for more than 33 years and held several senior roles, including Associate Deputy Attorney General, Head of the Cybersecurity Unit, Special Counsel for National Security, and Senior Counselor to the Assistant Attorney General for National Security. He is currently an adjunct professor at Georgetown University Law Center, where he has taught courses on cybersecurity and investigating cybercrime and received the Charles Fahy Distinguished Adjunct Professor Award. He has also taught a course on critical infrastructure protection at NYU School of Law. Leonard earned his undergraduate degree from Yale University and his law degree from Yale Law School. Leonard will be speaking on a panel on offensive cyber operations at CyberNext on October. 8.
Read Next
What States Can Learn from North Carolina’s Approach to Securing Government
As states across the country grapple with how to adopt AI responsibly, North Carolina offers a compelling case study - not because it has all the answers, but because it has built the institutional muscle to learn, adapt, and lead.
Developing a National Cybersecurity Strategy
Developing a national cybersecurity strategy is a critical investment a government can make to secure its future. This paper outlines the components and offers a framework with the tools to design, implement, and improve their strategies.
FedRAMP Signals Acceleration of Requirements for Machine-Readable Packages in the Rev5 Process
FedRAMP has proposed modifications to the Rev5 process in the newly published RFCs that could enact major changes and require Cloud Service Offerings to provide authorization packages in a “machine-readable format.”

